Making configuration changes to existing infrastructure is painful. Whether you are remediating a long list of Cloud Security Posture Management (CSPM) findings or upgrading a single database size, changing configuration en masse requires significant manual effort:
- Quantifying, prioritizing, and managing the impact
- Writing and reviewing Terraform PRs
- Coordinating and motivating developers to make the change
No wonder so many vulnerabilities go unremediated: developers aren’t cloud security experts, and are frequently without the guidance they need when writing IaC that fixes the problem. Remediation requests compound with multiple interrelated vulnerabilities, and security teams end up shouting into the remediation void.
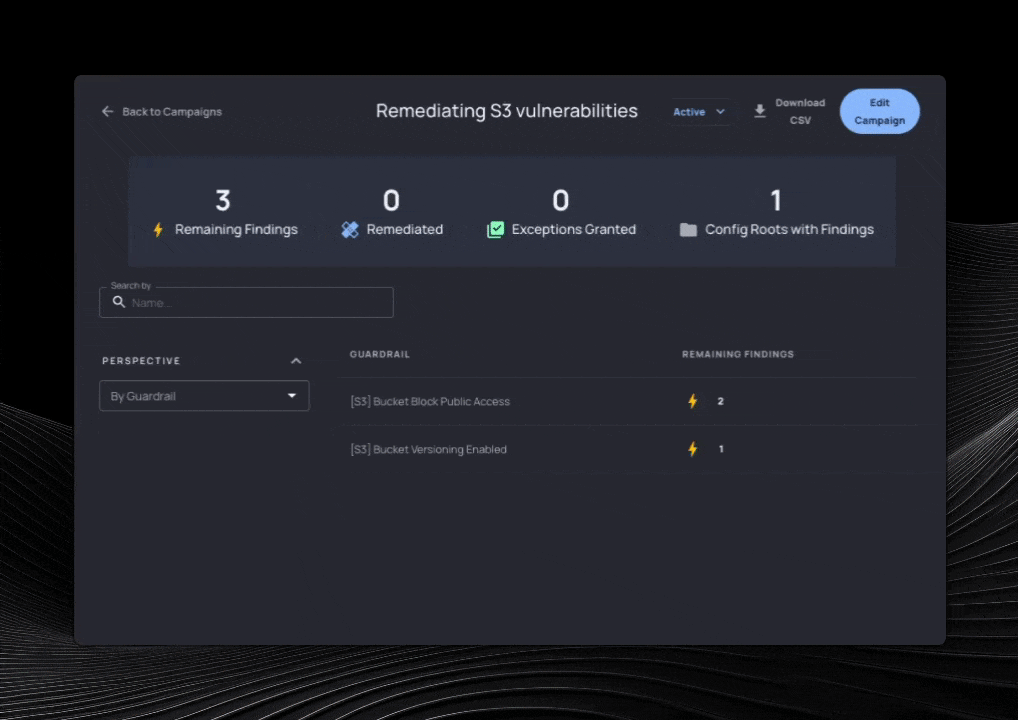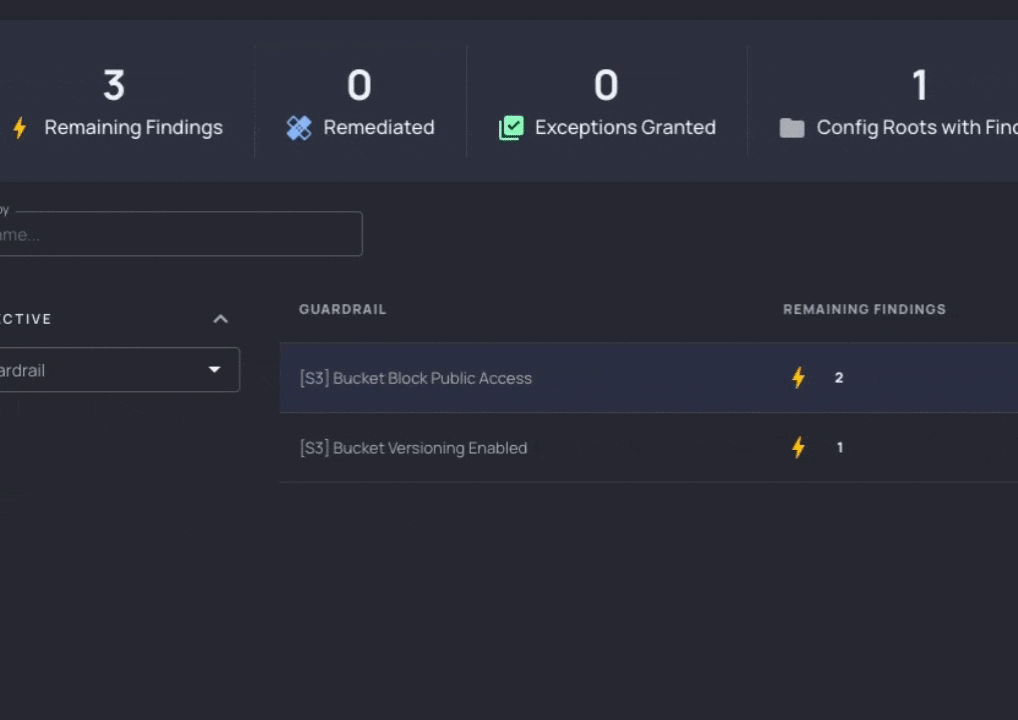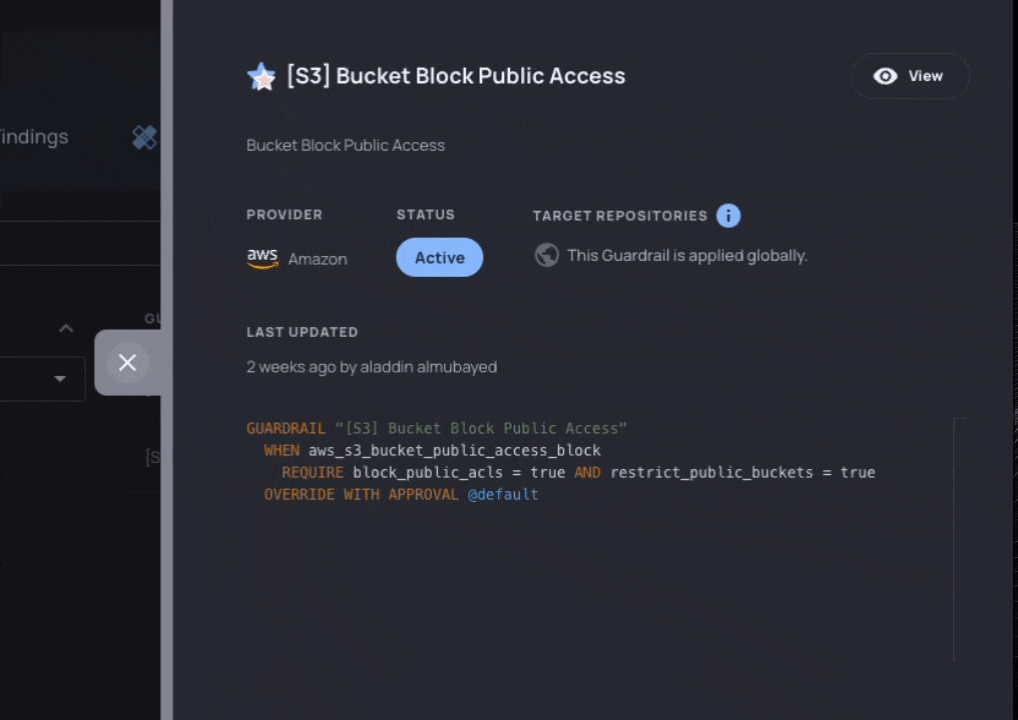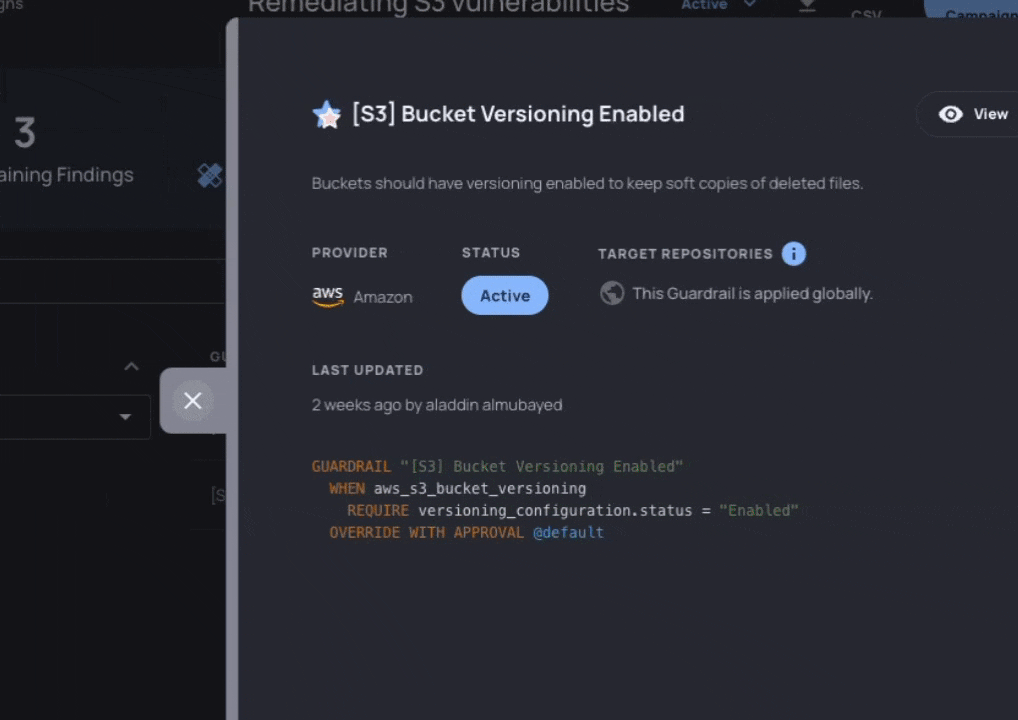
Today we are releasing Campaigns, a tool for changing existing cloud configuration. Campaigns give central teams the tools to define, identify, and help developers fix infrastructure that doesn’t meet expectations.
How they work
- Define: Choose policies (Resourcely Guardrails) that define the behavior you expect. Bundle multiple Guardrails to burn down all of your violations across teams, or target a single application’s database with a lone Guardrail.
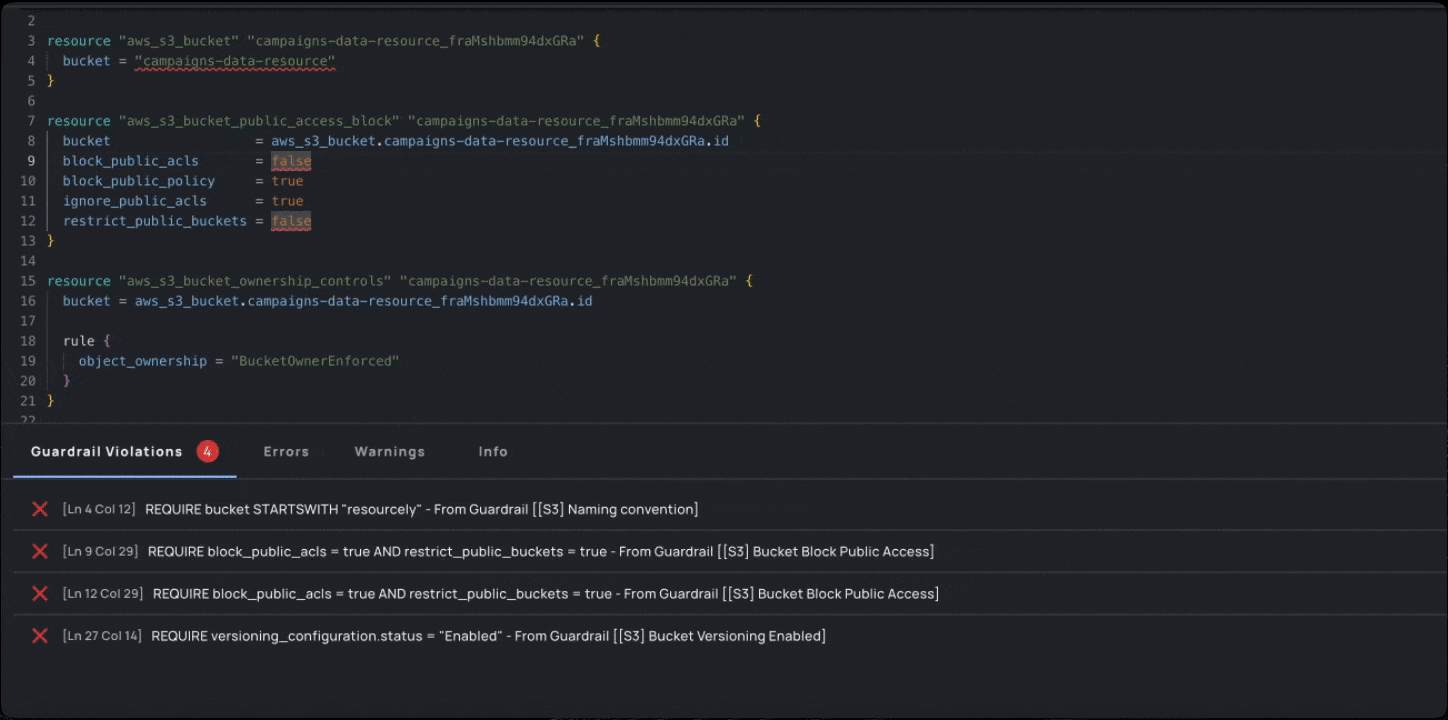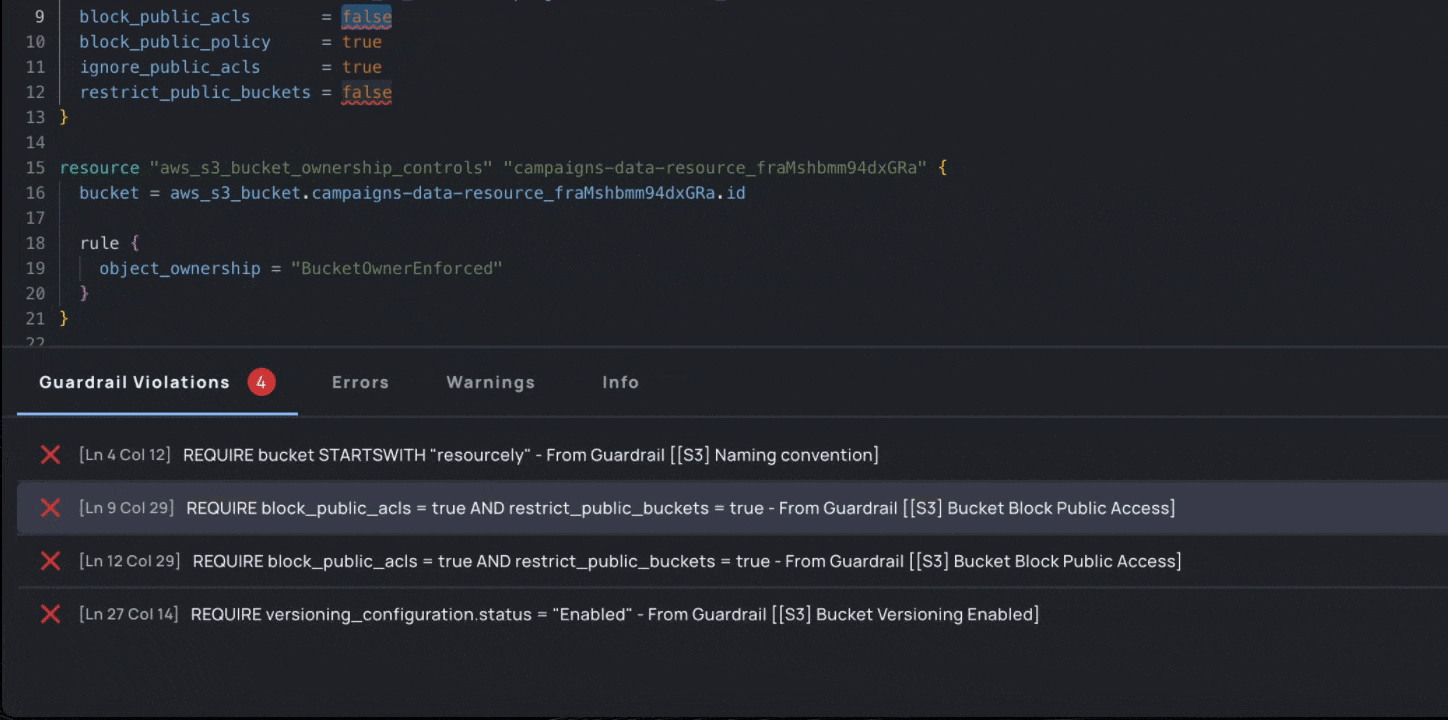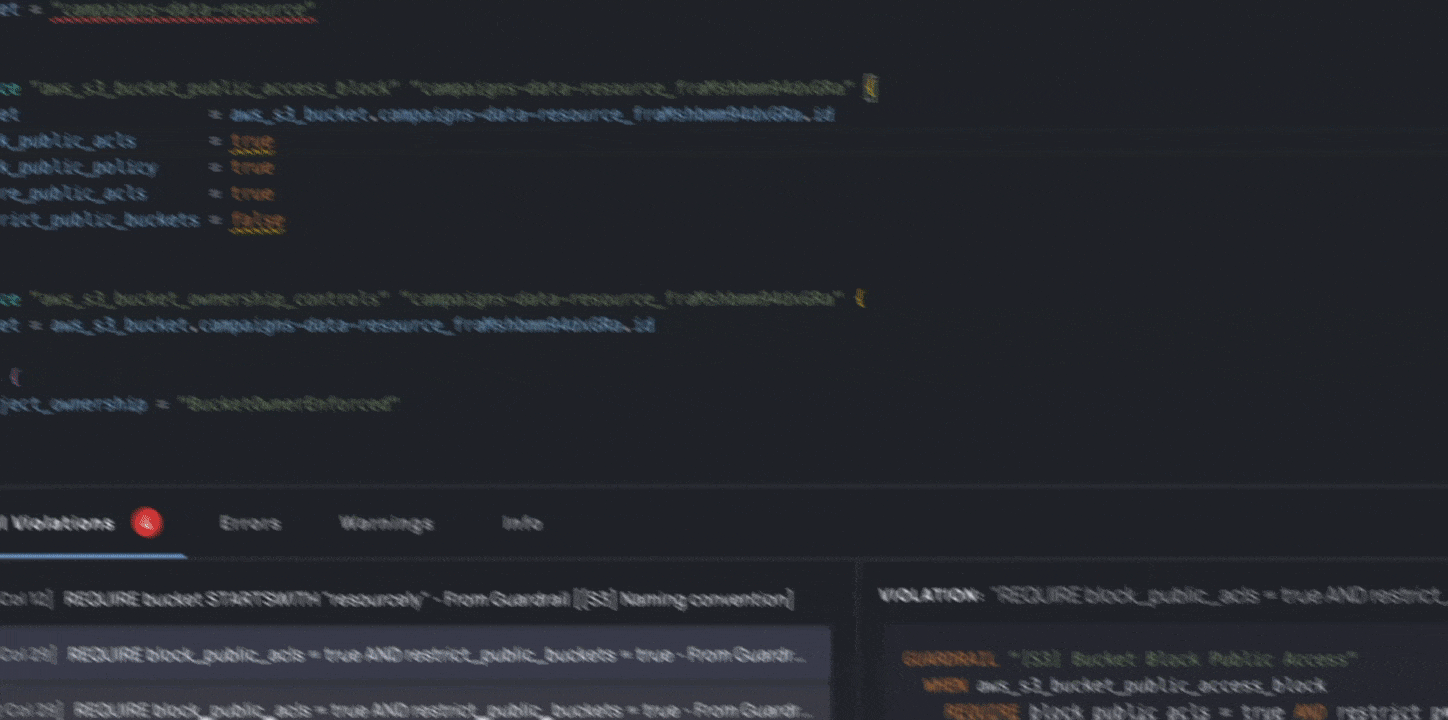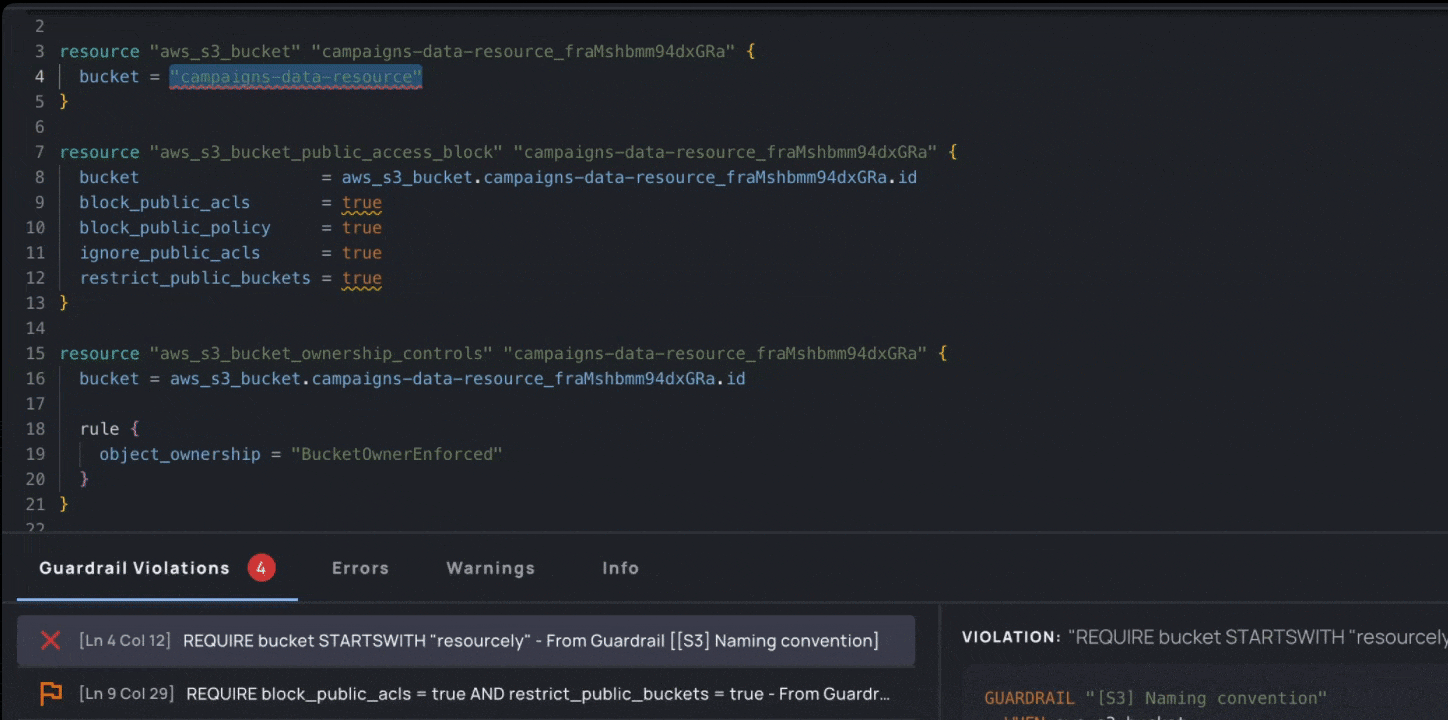
- Identify: Scan your environment and find the resources that violate the Guardrails you chose, using intuitive UI. Assign owners, exclude resources, and prioritize what is important.
- Fix: Track progress and guide developers to make configuration changes by taking them back to the specific lines of code where the violation occurs, showing them how to implement that change, and allowing for exception workflows where it makes sense.
Campaigns is integrated with your existing infrastructure stack: CI/CD, Terraform runner, and your infrastructure across every cloud.
For security teams
Consider a security team with hundreds of vulnerabilities their CSPM has identified that they want to fix, but they can’t fix them on their own. Not only would they not have the time to make all these fixes, but they can’t without potentially impacting production workloads.
With Campaigns, security teams can map their vulnerabilities to Resourcely Guardrails. Each vulnerability can be assigned to a developer, who is presented with the code that violates the Guardrail. A fix is suggested, and the developer can submit that fix as a PR or request an exception: fast-tracking developers toward implementing a fix without requiring them to research the correct cloud configuration or hunt through their code to understand the violation.
For platform teams
Now consider a platform team that wants to reduce costs and migrate all their AWS instances to a Medium or smaller. This would take manual work to scan your state file, track the affected resources, equip developers with the correct IaC, and project management efforts in a Kanban board or spreadsheet.
Instead, with the following Guardrail…
…you can help control costs while giving developers an exception for critical applications that may need a Large or greater instance size.
Try it today
Campaigns are meant to be flexible: no matter if you’re a security team, a platform team, or an individual developer with lots of cloud resources to manage and update. With Campaigns, simply describe your desired configuration and let Resourcely guide you and your developers through the rest.
Try Campaigns today with a free trial of Resourcely’s Enterprise tier today.